Looming behind the excitement at SC16 around new digital enterprise strategies is the growing menace of cyber-attacks. But in spite of these worries, the state of cybersecurity readiness at too many companies is woefully inadequate.
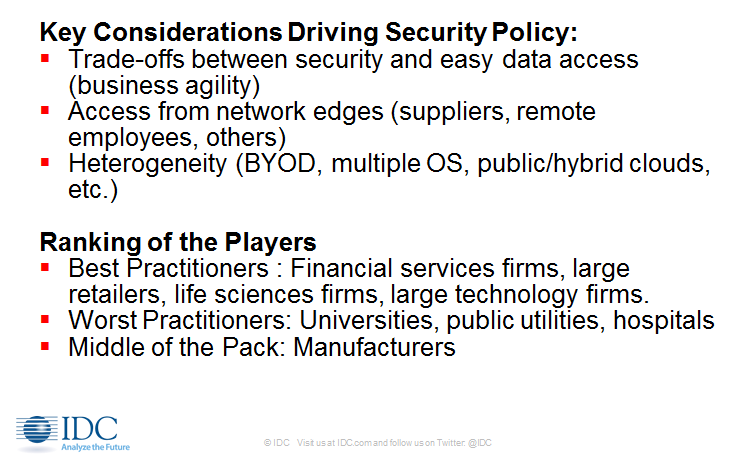
That’s the finding of Bob Sorensen, research vice president, HPC Group, at industry watcher IDC delivered at the analyst group’s annual HPC Update breakfast at SC16 this week in Salt Lake City. Sorensen’s message: If your company has the characteristics of a cybersecurity “worst practitioner” (which tends to be among public utilities, hospitals and universities – manufacturers are generally “middle of the pack”), the time to adopt new cybersecurity strategies is now.
IDC conducted a study of cybersecurity at 62 large industries in the U.S. and Europe across the financial services, technology, manufacturing, retail, hospital and academic sectors. Here are excerpts of his comments:
The State of Cybersecurity
The key concerns that came out in our study: Most US companies are underprepared to deal with cybersecurity threats. Even though there are lots of good best practices, they’re only being conducted by a small number of leading-edge firms. On average, firms are not availing themselves of what’s readily available, and that’s a cause for concern.
Detecting a breach can take up to two years. That’s really a disturbing concept, that someone could be nosing around corporate data that’s not only unprotected, not just to steal data, but to change it. Data integrity is a concern, the idea that the data you’re using to make critical decisions in research or business process environments may not be the right data, it may have been changed for nefarious reasons. It’s one of the silent concerns.
The Big Fear: Reputation Damage
One of the things we found with the Target breach, a very public intrusion, is that Target really didn’t take a huge financial hit on the actual intrusion itself. There was insurance in place, there was pushing off losses to the finance companies that Target deals with.
What we found, what really scares companies, isn’t the loss of dollars, it’s the loss of reputation, which brings with it a future loss of income that you simply cannot determine. Companies…can buy insurance for a particular hit, that’s a known quantity, but what they can’t do is figure out how that affects their line of business down the line. Which speaks in some sense to the idea that there’s probably a lot of cyber-attacks we’re not finding out about simply because it benefits these companies greatly to keep attacks under wraps as long as possible.
Malware Manners
We heard this time and again: malware people are conducing themselves in a very proper and organized manner. The thinking with a lot of them is…they don’t charge too much because they don’t want to kill the goose that laid the golden egg. (Malware practitioners think of it as) a very refined, respectable business to be in. You come in and say: ‘Give us some money and we’ll go away.’ You give them money and they do go away because if they don’t, no one’s going to give them more money. And if they ask for too much money there are going to be problems. So right now it’s a very genteel world out there for malware.
Conflicting Priorities: Security and Access

There’s a major tradeoff between security and easy access (to the network and to data). It’s something every business has to deal with. We asked questions about balancing security and processes, and the underlying goal is: ‘We have to do both, we can’t sacrifice our business plan for our cybersecurity.’ We found time and again even among the best practitioners in data security: Job 1 is conducting business, and that process is king. This is handed down from the board of directors of the company, and then they tell cybersecurity teams, ‘Make us secure under this realm.’
Proliferating Points of Attack
Heterogeneity is a problem: the idea of ‘bring your own device,’ multiple operating systems, clouds. There are lots and lots of end points out there, lots of way to enter a network, and these are things cybersecurity folks are definitely worried about.
We talked to the cybersecurity chief at Nike, he said he has 59 (network) access points to worry about every day because he has to make everyone who gets on the Nike website, who wants to look at the new and latest sneaker, has access, can order, can conduct business. That’s his job, and he has to work within those confines.
There is increasing access from the network edges. The one I would point out is suppliers. Supply chain issues I think are really interesting. More and more large industrial companies are increasingly tied electronically to their supply chain, and that is a real vulnerability….
Worst Practices: Wait and See
A lot of the worst practitioners really just buy insurance…. The worst practitioners time after time said, ‘We have the best tools, life has got to be good.’ The story we like to repeat: the companies that seem to be most sanguine with their cybersecurity infrastructure say: ‘We’ve never been hit before so we must be doing something right.’ They weren’t terribly forward looking when it came to actually making sure they were more secure….
Everybody (in the survey) had data breach plans, but… a lot of them were not IT-related. The thinking wasn’t to gather up forensics and figure out how to plug holes. It was how to deal with the publicity aspect, the legal aspects, the privacy concerns, the possibility of getting sued. This surprised us….
Best Practices: People vs. People
One thing we found is that the best practitioners see this as a people vs people battle. This is not a tool war where as long as you have the best software, as long as you roll out the patches when you’re supposed to, then life is good. It’s really about finding, hiring and retaining the best people to go after the people who are trying to get at you.
Best Practices: Be Proactive
An interesting concept that we see is that proactive cybersecurity team think in terms of educating the user base within their companies. They’re not just sitting back and making sure the patches are installed and making sure everyone changes their password every six months. It’s really more about reaching out…to the individual people within firms and making sure they understand their roles.
For example, one company closely watches social media. And they look for key events that they think could trigger a phishing attack. When it became known that Prince had died, they sent out an email to their entire company saying there’s a good chance you’re going to get an email in the next 24 hours asking if you want to see the Prince tribute video. So the idea is to proactively get employees to be aware of what their responsibilities are.
Another story we heard is about companies buying stolen credit card numbers. Not because they want to get involved in law enforcement but because it’s cheaper to buy stolen credit card numbers and put them in your database. So if someone tries to buy something with a stolen number you can kick them out. It’s an interesting, proactive way to do this.
So the good cybersecurity team isn’t waiting for problems, it’s going after solving them before they happen.

Data Scientists and Cybersecurity
Most companies aren’t using Big Data (for cybersecurity purposes) in the sense that we in the HPC community think about Big Data… When we asked companies why they weren’t using Big Data, they said they can’t find Big Data scientists who know how to do cybersecurity.
And when we went to companies that have lines of business that use smart data scientists, they said, ‘Yeah, they’re over there contributing to the bottom line of the company. We can’t bring them over to cybersecurity, they’re going to stay over there making money for the company.’
Virtual Cybersecurity Data Science
What I see in the future is really where HPC comes into play here. The goal for a lot of cybersecurity teams is real-time intrusion detection. They want to have a dashboard that tells them something odd has happened in the network. And a lot of folks think that deep learning – the idea that you have a system that monitors the steady state of the network and rises to the attention of humans where something has gone awry.
We’re going to see more efforts for high powered systems and deep learning to do real-time monitoring…almost as a way to get companies out of having to find data scientists. This might be an ultimate method toward dealing with cybersecurity… It’s something the HPC world is going to be involved in much more going forward.